Reverse-engineer the obfuscation process.
When you have it figured out, examine this pcap file to find the correct credentials and log in.
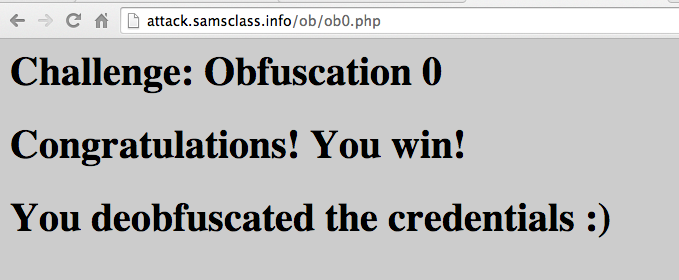
You can solve it yourself, but if you'd like some guidance, scroll down.
You should see this:

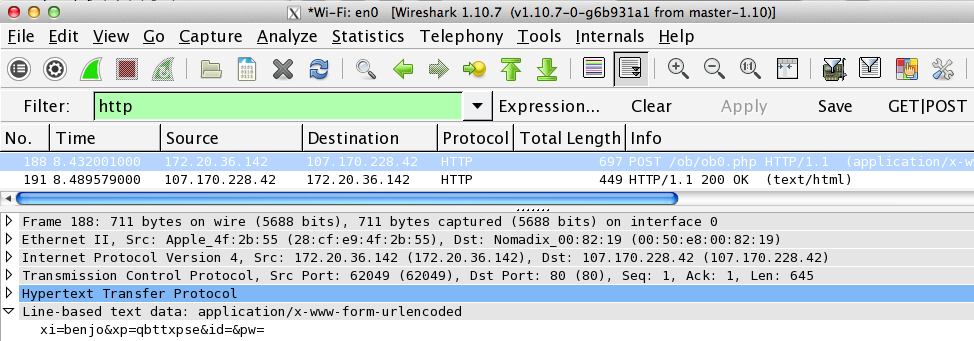
At the bottom, you see the "Line-based text data" which is sending two parameters:
xi=benjo
xp=qbttxpse
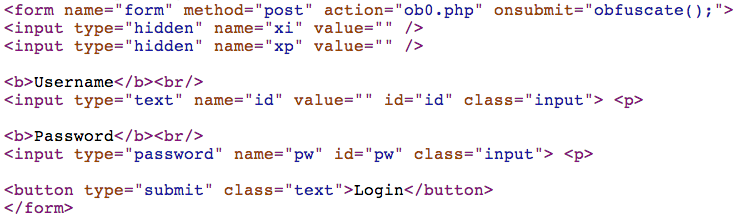
When the Login button is pressed, the onsubmit method calls a JavaScript function named obfuscate().
The scramble function performs a simple Caesar cipher, moving each character forward one step in the ASCII "alphabet", so "a" becomes "b", etc.
The obfuscate function simply scrambles both the UserID and Password and erases the plaintext versions.
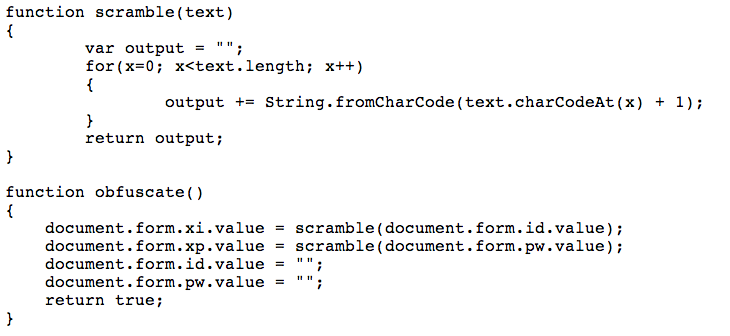
So to deobfuscate the credentials, open the pcap file and move each character one letter backwards in the alphabet to find the correct credentials.
When you get it right, you'll be able to log in and see this page: